[ad_1]
Advantages and implementation of DevSecOps
The IT project is based on three pillars: developers, system administrators, and testers. Previously, they worked separately: programmers tried to write and give the code as quickly as possible, and system administrators only cared about the system’s stability. If low—quality code got into production, it paralyzed the output of the product: testers had to spend time searching for and eliminating errors. That’s why the DevOps culture was invented, when administrators and developers agreed on the criteria for “accessing” code to further deployment. The next logical step was the transition to DevSecOps. Let’s figure out what is the peculiarity of DevSecOps companies and why DevSecOps consulting is necessary for business.
Let’s understand the concepts
The DevOps methodology emerged more than a decade ago to bring together two teams — developers (Dev) and Operations (Ops) — with the goal of fast software delivery. According to DevOps, the speed of rolling out a software product increases due to continuous cooperation, communication, automation, and integration. If something breaks during development, the flaw can be detected and corrected in advance.
The overall goal of the teams is to speed up development and implementation, get a practical effect and reduce the number of cases of code being returned for revision. Previously, companies updated applications several times a year, and now the introduction of DevOps has allowed them to innovate faster and minimize the cost of errors. Switching to DevOps has become the key to the success of Kaiser Permanente, Starbucks, Yahoo, etc. For example, in branches where Kaiser Permanente has deployed DevOps “squads”, employees respond to service requests 47% faster and to change requests 53% more efficiently.
The SecOps methodology only considers the cooperation of two teams: Cybersecurity (Sec) and Operations (Ops). Its goal is to increase reliability by conducting security testing at all stages of the software development lifecycle (SDLC). With this position, all SDLC participants are responsible for the product’s safety and are involved in fixing vulnerabilities.
Unlike DevOps, security in SecOps becomes a central event, not a secondary one. Thus, specialists organize permanent protection, reduce the cost of violations, prevent threats, establish cooperation within the team and provide the customer with a strong business reputation.
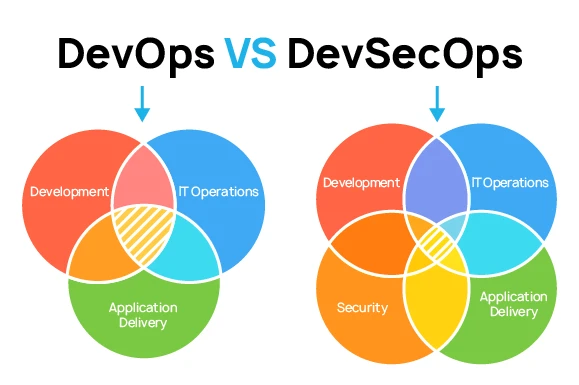
DevSecOps is an improved formula based on previous experiences. This methodology integrates DevOps with SecOps into a continuous cycle of software development, technological operations, and cybersecurity.
Specialists do not hesitate to choose between development speed and security: DevSecOps implies a healthy balance of these processes. Thanks to the use of a flexible structure, teams of programmers and testers can collaborate on an ongoing basis.
DevSecOps vs DevOps
DevOps as a Service is focused on speed, which often leads to security specialists not having time to react. DevOps updates the application in brief periods (hours or days), which can significantly outpace the security team’s speed.
If the vulnerability search is not automated properly, the DevOps pipeline will either slow down or stop providing proper security hygiene. This will lead to weaknesses: unreliable code, incorrect settings, etc. Such consequences provoke downtime or, worse, are used by intruders. Thus, DevOps guarantees fast and frequent development cycles, but outdated security practices can negate even the most effective DevOps initiatives.
Like DevOps, DevSecOps can be called a separate philosophy introducing security techniques into the DevOps process. From the very beginning, SDLC DevSecOps has been working to ensure the application’s reliability using various methods.
For example, the developers have implemented a user authorization form in the application and expect that no one will be able to bypass it. But then it turns out that they didn’t consider some critical points: the password is not transmitted securely, it is unstable, the authorization form can be circumvented, etc. Such situations are easily avoided using the DevSecOps methodology.
To implement DevSecOps, you may need tools that don’t affect the product but are relevant to its creation. These are trackers for maintaining repositories or bug reports, virtual environments where debugging and testing of programs take place, servers for deploying test environments, and checking the operability and scaling of applications. As a result, changes are constantly being made to the company’s infrastructure. The rapid exchange of information between programmers and testers is the cornerstone in ensuring the entire organization’s security.
In other words, DevSecOps is an attempt to fully implement security testing in the continuous integration (CI) and continuous delivery (CD) pipelines.
The culture implies that developers will receive the necessary knowledge and skills in order to avoid errors in the code and be able to fix them before they get into release with the product. With DevSecOps, security testing is carried out by the developers themselves and the detected problems are also eliminated by them.
DevSecOps is built-in security. If it remains at the end of the development pipeline, organizations implementing DevOps may return to the long software creation cycle they initially tried to avoid.
Advantages of DevSecOps implementation
More and more companies are implementing automated security testing as part of CI/CD pipelines, but the results may not be immediately noticeable because this is a long-term solution.
DevSecOps provides many advantages:
- Costs are reduced by early detection and prevention of troubles.
Statistics collected by Veracode show that since the adoption of the DevSecOps methodology, the percentage of applications without serious problems has increased from 66% to 80%.
For example, a certain library, “A” is needed to work with the software. But it depends on another library, “B”, which also depends on the library “C”. But “C” is vulnerable. Therefore, the developer cannot use any of these three libraries. And what if you need to evaluate the security of twenty or more components for a software product or explore alternative open-source libraries? As you can see, this is an important and complex process.
The ability to assess risk in advance will allow project managers and developers to create reliable software from the very beginning, rather than waiting for the product to be released and vulnerability assessment will be impossible. In practice, this means huge savings in man-hours and resource management costs.
- The speed of application recovery increases.
The average time to fix errors in the daily checked applications is 19 days. Making edits to the program, tested once a month, takes about 68 days. As a result, more frequent checks increase the chances of a quick response to vulnerabilities.
No one knows how many software packages contain reliability defects in a vast open-source ecosystem with millions of repositories. Given the enormous volume, it is impossible to predict this without any security automation.
The integrated DevSecOps solution, which supports automation, can help programmers figure out if they are inadvertently using any open-source libraries with known vulnerabilities. This happens before they start coding the rest of the modules of the software project.
- Threat monitoring allows the brand to form a positive image and optimize sales.
Research by the University of Arizona has established a pattern: qualitative updates of the program contribute to a threefold increase in its survival rate. In a rapidly changing market, this is a worthy competitive advantage.
- Overall, security is improving.
Statistics clearly demonstrate the importance of monitoring the application’s reliability. According to the World Economic Forum, in 2019 the number of attacks on IoT devices increased by 300%, and in 2021 their number amounted to 1 billion. At the same time, the share of successful criminal investigations is only 0.05%. Security may not always be the number one task of programmers because they are time-bound and don’t have knowledge in this area. DevSecOps motivates them to be more interested in creating reliable code.
DevSecOps implies comprehensive management of cyber threat analysis systems, tracking, and notification of hacks. This methodology develops a culture of openness and transparency from the earliest stages of software creation because each participant is responsible for security.
DevSecOps ensures that the reliability of the software is a priority, and the following steps are regularly performed:
- Security requirements are documented and implemented;
- Security is built into the project;
- Security is the first thing developers consider before writing code;
- Security testing is a priority in the development and execution of tests;
- Security is considered for any changes to the system.
The cultural and technical shift towards DevSecOps helps companies deal with security threats quickly and efficiently. For example, if the team discovers in advance a poorly designed application that is not able to scale in the cloud, this will save time, resources, and computing costs.
Although no program is 100% reliable, the DevSecOps implementation helps to bring the degree of security to the maximum figure. By applying this approach, companies strengthen trust in their applications, form a positive image, and increase customer loyalty.
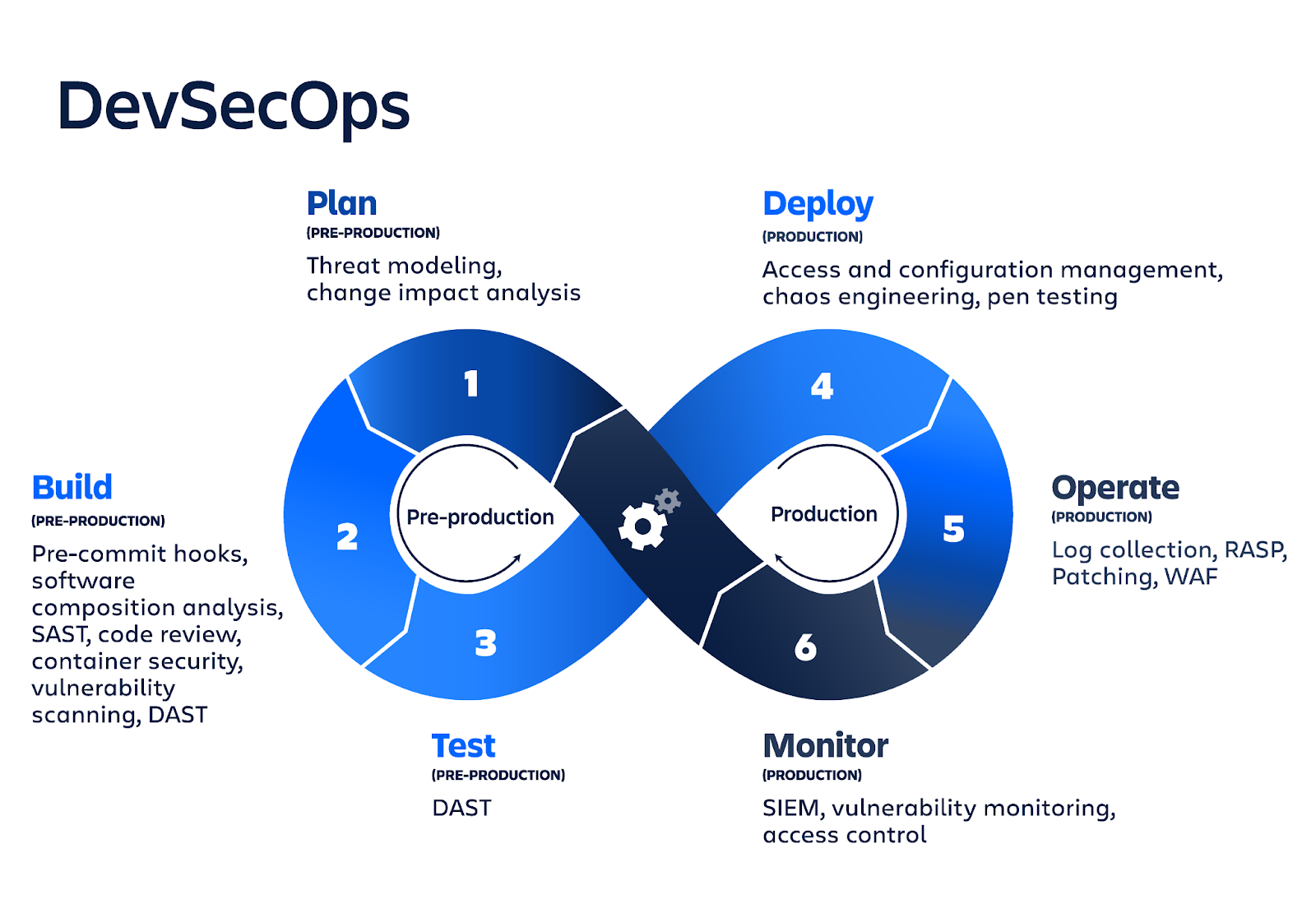
How to implement DevSecOps
DevSecOps implementation requires a change in the mindset of all parties involved: both management and engineers. With this methodology, security becomes part of every step of the operation.
It is important for SDLC participants to know their role in the cycle, and communication channels should be configured so that security specialists can provide the necessary information at any time.
Proper documentation is required to implement DevSecOps. A successful product should be convenient and safe, and the requirements document should contain a guide to its creation.
DevSecOps uses security testing automation, which allows you to test the code before it is deployed. If possible, tests are performed with source code (static analysis), compiled or interpreted code. Deployed software at the finish line must pass a set of security tests and immediately roll back if it fails at least one check.
Automation is important both for creating a program and for its support. After the software is deployed, network tracking tools should analyze its operation and report any abnormal behavior in order to eliminate the attack.
The transition to DevSecOps requires a significant rethinking of the software creation processes. The introduction of the new methodology will lead to writing code with fewer defects, which means a reduction in the number of failures and emergencies.
Conclusion
The increase in the number of cyber attacks and the improvement of the methods by which attackers steal confidential data suggests that application security needs to be given the utmost attention. Any such incident can lead to lawsuits and fines, loss of customers, and income.
There is no fantastic way to find out if your application is safe and if there is any threat to business. Following best practices, such as ordering DevSecOps services, can significantly reduce risks and protect the company from the very beginning.
[ad_2]
Source link

