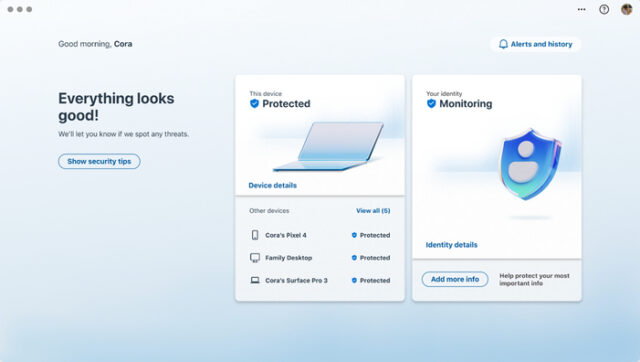
[ad_1] This site may earn affiliate commissions from the links on this page. Terms of use. … Microsoft Adds Identity Theft Monitoring Service to 365 SuiteRead more
Computer
Begone, polygons: 1993’s Virtua Fighter gets smoothed out by AI
[ad_1] Enlarge / “Sarah” from Virtua Fighter gets an AI makeover thanks to Stable Diffusion and … Begone, polygons: 1993’s Virtua Fighter gets smoothed out by AIRead more
Best Buy Portable Monitor You Should Know > 9ja Tide
[ad_1] A portable monitor is a monitor that can be carried everywhere. It’s not as big and … Best Buy Portable Monitor You Should Know > 9ja TideRead more
5 Best Men Hoodies On Amazon 2022
[ad_1] If you need a good quality hoodie that you can wear anywhere, these are the … 5 Best Men Hoodies On Amazon 2022Read more
What Is Matter? We Explain the New Smart Home Standard (2022)
[ad_1] The ideal smart home seamlessly anticipates your needs and instantly responds to commands. You shouldn’t … What Is Matter? We Explain the New Smart Home Standard (2022)Read more
Why Post-Project Evaluation is Critical to Future Success
[ad_1] Many people avoid one of the most crucial steps of any project: the post-project evaluation … Why Post-Project Evaluation is Critical to Future SuccessRead more
Mystery Person in Elon Musk Texts is Ex-Wife Talulah Riley
[ad_1] Talulah Riley attends the British Academy Film Awards 2022 Gala Dinner on March 11, 2022 … Mystery Person in Elon Musk Texts is Ex-Wife Talulah RileyRead more
Amazon sues Washington state regulators, alleging Constitutional violation in warehouse safety case – GeekWire
[ad_1] The case focuses on Amazon’s fulfillment center in Kent, Wash. (GeekWire File Photo / Kevin … Amazon sues Washington state regulators, alleging Constitutional violation in warehouse safety case – GeekWireRead more
Images of DART Impact Show the Differences Between Webb and Hubble
[ad_1] This site may earn affiliate commissions from the links on this page. Terms of use. … Images of DART Impact Show the Differences Between Webb and HubbleRead more
Mystery hackers are “hyperjacking” targets for insidious spying
[ad_1] Marco Rosario Venturini Autieri/Getty Images For decades, virtualization software has offered a way to vastly … Mystery hackers are “hyperjacking” targets for insidious spyingRead more